What is a Mobile Application Penetration Test?
Mobile application penetration testing involves evaluating the security of mobile applications running on platforms like Android and iOS. This testing aims to identify vulnerabilities in the mobile app itself, as well as in the backend services it interacts with. The goal is to ensure that mobile applications do not expose sensitive data or functionality to attackers, thereby protecting users and the organization's data.
During a mobile application penetration test, testers assess the app for issues such as insecure data storage, improper session handling, weak encryption, and insufficient input validation. They also examine the app's interactions with backend services, looking for vulnerabilities in the API endpoints and server configurations. Common tools used include dynamic and static analysis tools, as well as manual testing techniques. The findings are compiled into a detailed report, which includes recommendations for improving the security of the mobile application. The ultimate objective is to ensure that mobile applications are secure, resilient, and compliant with industry standards, thereby providing a safe user experience.
Frameworks and Standards
OWASP Mobile Security Testing Guide (MSTG): Provides guidelines and best practices for mobile application security testing.
MASVS (Mobile Application Security Verification Standard): A standard for mobile application security.
PTES: Provides a lifecycle for penetration testing engagements
Common Tools we utilize to assess your Mobile Application:
MobSF (Mobile Security Framework): An automated mobile app security testing framework.
Burp Suite Pro: A comprehensive web application security testing tool that is also useful for proxying and testing API requests that a mobile application consumes.
Frida: A dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers.
Drozer: A comprehensive security audit and attack framework for Android.
Objection: A runtime mobile exploration toolkit.
Let Rarefied help assess your mobile application today!
How a Security Test is Performed
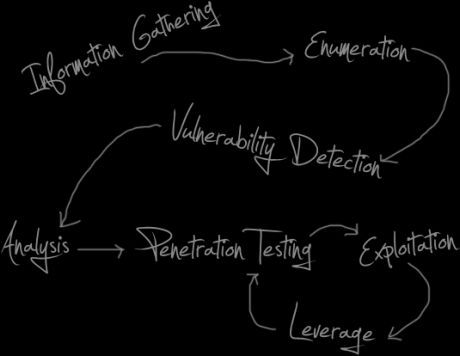
Our penetration testing methodology is based on a variety of security standards including, but not limited to, NIST, OWASP, and industry best practices. We put each target through this process to ensure a quality test every time and to meet our service commitments. Our test results can be used to support compliance standards (PCI, HIPAA, etc.) or best practices.
01
Information Gathering & Enumeration
This is the most crucial stage of the assessment. In this phase, we learn everything we can about your environment by assessing technologies used, possible attack points, open ports, and anything else publicly discoverable. What we find here serves as the baseline for all future tests.
02
Vulnerability Detection
We use a hybrid approach of manual testing techniques and automated scanning tools to look for possible vulnerabilities in your environment.
03
Analysis
Now it's time to develop a plan. Based on what we have learned up to this point, we decide which attack vectors to further pursue, and start testing.
04
Vulnerability Exploitation & Leverage
This is where the real fun begins. A successful attack is almost always the result of chaining vulnerabilities together until the target is fully compromised. This is typically a circular process, in which vulnerabilities are tested for, exploited, and then leveraged to test for more issues. The process repeats itself until the goal is achieved.
We deliver a formal report detailing our findings
We'll test your web applications, network hosts, APIs, and mobile applications for security issues. We'll then discuss the issues with your team and provide a report detailing our findings. This report can be used in support of compliance (PCI, HIPAA, etc.) or best practices.
What comes next?
Once we have completed our testing, we'll work closely with your team to make sure they understand the issues we have uncovered. Our goal is to ensure that our rigorous security testing provides you and your team with peace of mind that you are implementing secure coding techniques correctly and following security best practices effectively.
Ready to get started?
We look forward to discussing your security testing needs.